As attackers’ tactics evolve, risk officers with enterprise risk mandates need new tools to keep pace
The number of cyber attacks continue to soar. CISOs and Risk Officers should focus more closely on understanding the intensity of the peril, not just measuring defensive posture, in order to make better risk-informed decisions. The risk from cyber fundamentally is a human behavior risk that requires a risk management approach that adjusts for realtime to changes in intensity of attackers’ behavior.
By any measure, cyber attacks are at an all-time high. A recent QBE report suggested the number of “disruptive and destructive global cyberattacks” taking place each year is set to increase by 105% to the end of 2024 compared with 2020 levels. A steady stream of data from large cybersecurity providers like Secureworks, Mandiant and CrowdStrike indicate similar trends, specifically for ransomware.
In 2023, Mandiant observed ransomware incident response and data site leak victims[1] were at an all-time high.
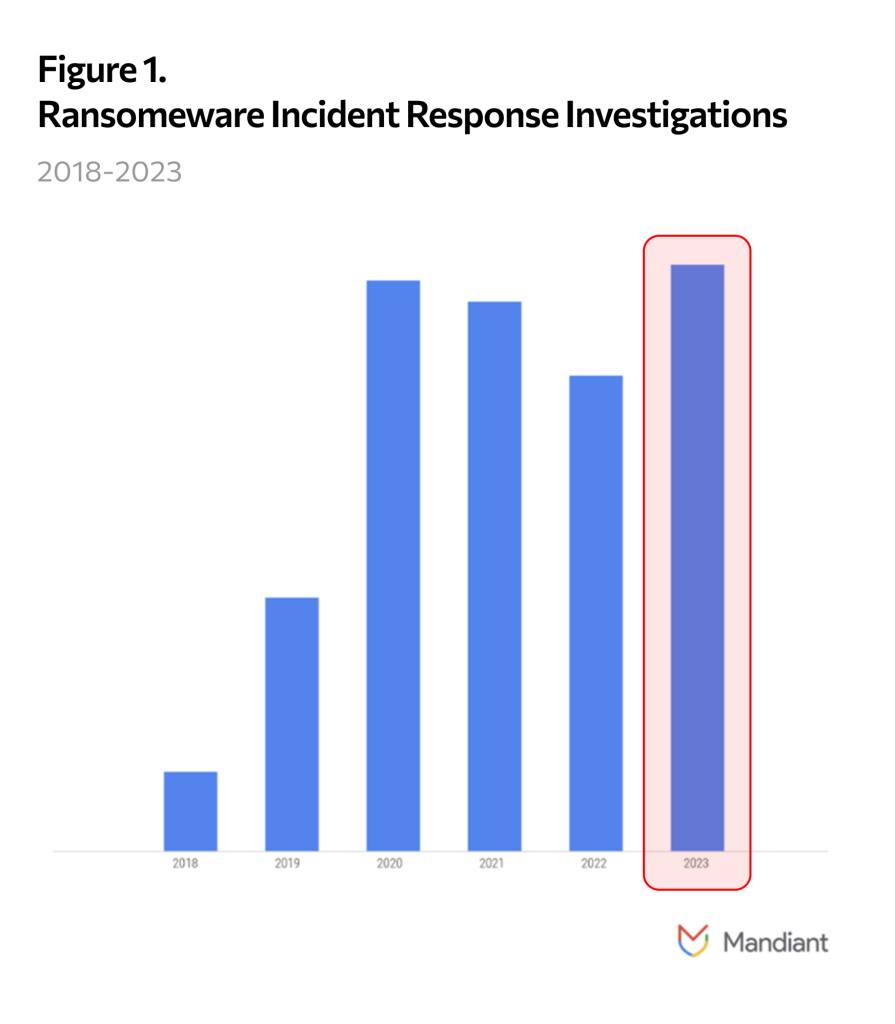
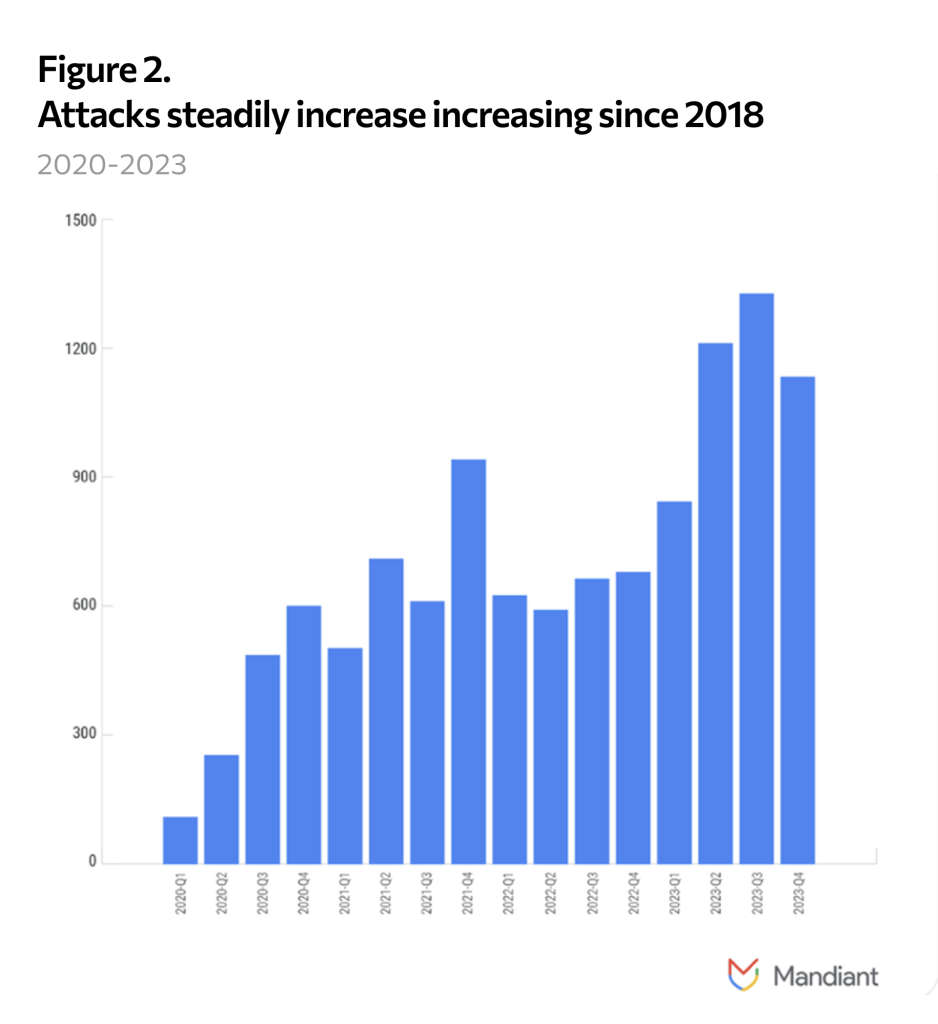
According to NetDiligence’s recent claims report, ransomware and business email compromise were the two leading causes of loss, comprising 39% of losses in 2023.
Look beyond claims data to understand the risk
Some claims data suggests the primary causes of losses can most often be tied to things like:
– Multi-factor authentication (MFA) not being mandated for remote access
– Vulnerability management (patching) not keeping up
– Vulnerable services exposed to the internet.
For most large companies, practices like MFA are well established. But as we’ve outlined in previous CyFi™ notes, attackers are increasingly turning to ways to circumvent these controls. That is why, risk managers and security teams need to look at actual attacker behavior relative to their company to understand the intensity of the cyber risk, not just measuring defensive posture.
IBM identified credential theft as the biggest shift they observed in cyber in 2023. According the company’s recent report, valid account compromises accounted for almost one-third of global cyberattacks last year, making them the most common initial access vector for threat actors. IBM observed a 71% increase in the volume of valid account credential attacks in 2023.
Numerous high-profile breaches, like MGM and Caesars, have illustrated the limitations of controls in the face of attackers increasingly adept at working around them and utilizing them to their advantage.
In a breach reported just last week involving security company ADT, an attacker breached ADT’s systems using compromised credentials obtained from a third party.
What is a social engineering attack?
A social engineering attack is a good example of what cyber as a human behavioral risk looks like in practice. Secureworks’ incident response team undertook two engagements in early 2024 that involved social engineering tactics most often associated with a criminal group known as Scattered Spider, the same group believed to have been behind the MGM breach. Both engagements involved the attacker calling into the victim’s help desk. In one case, the threat actor called to get their own cell phone number enrolled in MFA so they could respond to MFA requests, rendering this control ineffective.
The attacker was able to access the network and conduct post-compromise activity but was reportedly unable to achieve their objectives. However, this social engineering tactic (behavioral element) highlights how attackers are increasingly using best security practices against companies to go around controls and gain access to networks and company data for financial gain.
Source: Secureworks
Charles Henderson, global managing partner and head of IBM X-Force, said: “Rather than a technology shift, it is a business strategy shift on the part of threat actors. They are maximizing return on investment by taking the low-cost method of entry.”
This underlines why cyber is fundamentally a human behavioral risk that requires a forward looking approach that can adjust for realtime changes an organization’s risk intensity.
So What Are Risk and Security Teams To Do?
The job of the risk and security teams still come down to understanding, managing and transferring risk. Cyber risk is driven by human attackers who adapt their behaviors constantly in order to get around controls put in place to prevent their access to networks. Relying on an approach to understanding your risk that relies too much on measuring the companies defensive posture overlooks this fact.
According to Mandiant, 54% of organizations first learned of a compromise from an external source and only 46% first identified evidence of a compromise internally. “Cyber breaches that are not detected and contained early can end up being 1,000 times more expensive than those that are, the difference between a €20,000 loss turning into a €20 million one,” according to Rishi Baviskar, Global Head of Cyber Risk Consulting, Allianz Commercial.
Understanding the intensity of attacker activity relative to the company informs better resource allocation decisions (the ‘manage’ piece) so risk and security teams can prevent a loss rather than just recover faster from one. It is also now possible for risk and security teams to do this. The CyFi™ Platform bridges the gap between the risk and security teams. Leading companies like DS Smith that use the platform as part of the company’s enterprise risk framework are demonstrating what this looks like in practice.
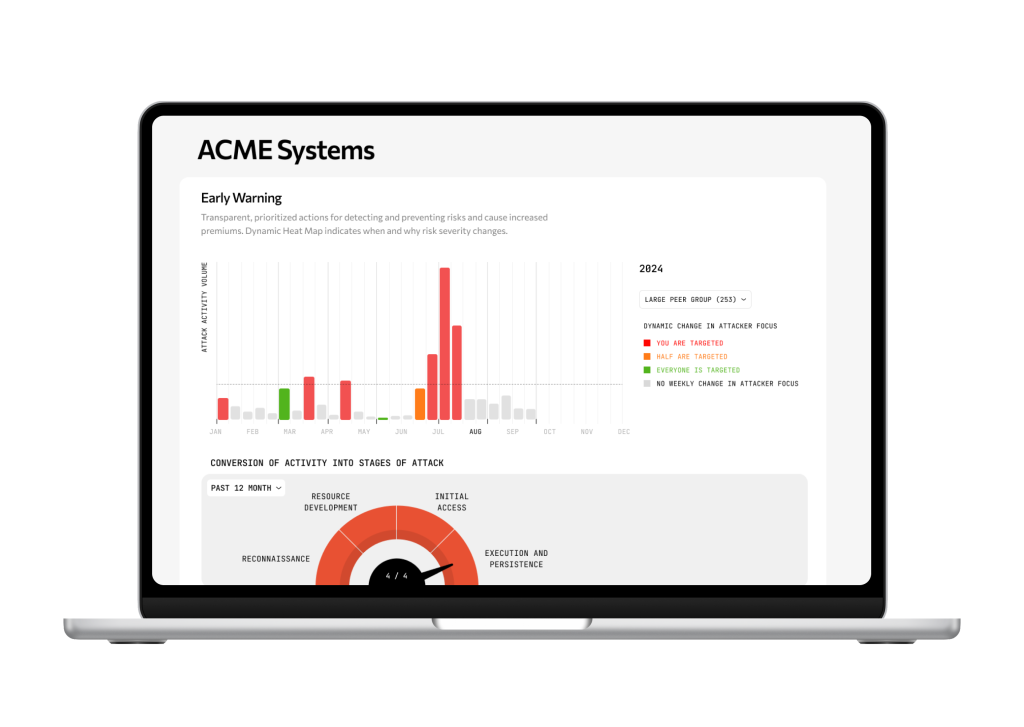
Every large organization has security blind spots that can increase the probability of a breach. This picture changes constantly based on what attackers are doing. Identifying those blind spots by understanding the intensity of your cyber risk in real time is now possible.
It’s also necessary in order to structure the right risk program and build the bridge as a risk manager with the security team so the risk can be managed proactively. It could be the difference between a €20,000 loss or a €20 million one.
[1] Data site leak: A website or online platform where sensitive information is stored has unintentionally exposed that data to unauthorized individuals, usually due to poor security practices, system vulnerabilities, or human error, making private information more accessible to criminal actors.