Increased digitization and third party outsourcing turn supply chain strengths into liabilities.
Pursuit of financial gains from digital transformation results in companies having less control over risks.
Four events in recent weeks have again drawn attention to cyber supply-chain risk for large companies. Collectively, the events highlight how the investment in technology and outsourcing of operational functions to third parties has expanded attack surfaces, increasing exposure to constantly evolving attackers. This has left risk and security teams with less control over the risk. Increasing digitization also means the operating models of companies are beyond the insurance market’s one-size-fits-all approach to assessing the risk.
There are things risk officers and CISOs can do to get more control over this part of the risk by monitoring threat activity towards key suppliers and utilizing risk metrics specific to the business, not a one-size-fits-all approach.
Blue Yonder
Blue Yonder, a US-based supply chain software company that serves many of the world’s largest grocery store chains, suffered an attack on November 21. The incident reportedly impacted its managed services hosted environment, but Blue Yonder’s Azure public cloud services remained unaffected. Two of the UK’s largest grocery store chains, Sainsbury’s and Morrisons were disrupted. “We have reverted to a backup process, but the outage has caused the smooth flow of goods to our stores to be impacted,” said a spokesperson from Morrisons.
As of November 24, the company said it still did not have a timeline for the full restoration of its IT systems.
Microlise
British telematics business, Microlise, confirmed in November that hackers compromised company data in an attack that took place in October. The attack affected many of its customers, including reportedly disabling tracking systems and panic alarms on British prison vans and impacted some of DHL’s delivery tracking service.
MOVEit: Delta and Amazon
This month, Delta and Amazon both confirmed that employee data was stolen by hackers that exploited the MOVEit vulnerability, a third-party file-transfer tool created by Progress Software. The breach is reported to have affected as many as 2,773 organizations, exposing 96 million individual records.
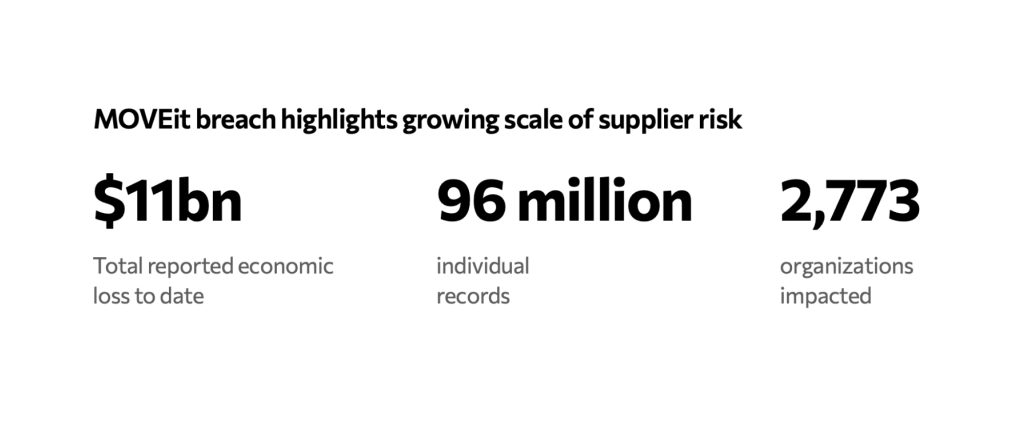
It was believed to have been limited to contact details of employees but has created an opening for more sophisticated social engineering attacks by hackers using this information in future. It is also the latest IT incident for Delta following the CrowdStrike outage this summer that cost the Atlanta-based airline over $500 million.
Palo Alto vulnerability
Palo Alto, a $126bn cybersecurity provider to many of the world’s largest companies, announced on Monday, November 18 that a vulnerability was discovered via its PAN-OS management interface that enables hackers to exploit a bug. “Palo Alto Networks has observed threat activity exploiting an unauthenticated remote command execution vulnerability against a limited number of firewall management interfaces which are exposed to the Internet,” the company said. In the announcement, the California company urged customers to configure the product correctly in accordance with its recommended best-practice guidelines. U.K. cybersecurity nonprofit, The Shadowserver Foundation said it found about 11,000 IP addresses exposed to the vulnerability. By Friday, November 15, the total number had dipped to about 8,700.
In pursuit of connectivity and efficiency, risks inevitably grow
A company like Microlise is a byproduct of digital transformation investment across transport and fleet, defense, and security and even agriculture. The company’s stated purpose of increasing operational efficiencies, improving customer satisfaction, and lowering costs are at the core of why companies have invested trillions in digital transformation.
An excerpt from DHL’s annual report on ‘yield management’ speaks to why tools like Microlise, which center on scalable automation, are so critical:
“Strong margin in supply chain supported by high quality delivered through our strategic solutions and scalable automation; pricing increasingly based on value we deliver to our customers, with support of digital tools.”
Blue Yonder’s tagline is a perfect encapsulation of today’s digitized supply chains: An AI-powered, autonomous, end-to-end supply chain network transforming how you run your business and turning uncertainty into opportunity.
Companies have used Progress Software’s MOVEit file-transfer tool because it claimed to offer secure and reliable file-transfer capabilities across networks, supporting task automation, data security and, ironically, compliance with data protection regulations like GDPR and SOX. This tool in fact has exposed impacted companies to potential GDPR liabilities instead.

In pursuit of technologies like this and the financial gains companies hope that come with them, this outsourcing has also greatly expanded a company’s attack surface.
What does this mean for the CISO and Risk Officer?
The goal for risk officers is not to have an immutable risk management strategy. But they are looking for one that reflects their business models (and risks) of today, not ten years ago. Since supplier risk is very much a part of a company’s overall economic loss risk due to cyber, more risk officers are seeking a clearer understanding of the changing risk, how to price it more accurately, and better control it.
CISOs and the security team need to know where the highest risks exist among third parties in order to better manage them. With the Intangic CyFi™ Platform, for the first time risk officers can help CISOs see this threat activity at scale across the supply chain on an ongoing basis. Suppliers that are being attacked more than their peers are at higher risk of a large breach. As a result, they can pose greater vulnerabilities to the companies they service.
By seeing spikes in risk levels with suppliers before the large breach occurs, CISOs and the information security team can prioritize possible preventative steps.
CISOs sometimes then point out, “but even if I know what suppliers are at higher risk of a potential breach, the preventative actions I can take are limited.” As a starting point, this data enables the CISO and risk officer to quantify the risk in financial terms so they can incorporate supplier risk into overall risk pricing.
Risk transfer strategy that reflects metrics specific to business
Leveraging a captive and with this advanced knowledge of supplier risks, risk officers can make more informed decisions about when to secure a contingent business interruption (BI) policy or a third-party BI endorsement in a liability policy. This can help risk and security teams more dynamically protect against the downside of a high-risk supplier.
Risk officers and CISOs need better tools to manage the dynamic risks of today’s highly digitized operating models. Moving from a one-size-fits-all approach, these are ways the two can work together to more dynamically protect against the downside of high-risk suppliers.
These dots represent the min and max of the range:
— 2015: BPO spending represented a smaller fraction of IT budgets – 10-12%
— 2020: By this year, the allocation increased to approximately 14-16%of IT budgets,
— 2023: The share allocated to BPO vendors rose to about 18-20%.