Companies can better manage supply chain risk when the CRO and CISO work together
What happened
TeamViewer, a remote global software provider, disclosed a hack detected by the company’s security team a couple of weeks ago. The story is a reminder of the supply chain risks companies are increasingly contending with. This followed the large Snowflake breach just weeks earlier, which is known to have impacted 165 of the AI Data Cloud platform’s customers, including Ticketmaster and Santander Bank.
TeamViewer attributed the attack to government-backed hackers working for Russian intelligence, known as APT29 (and also Midnight Blizzard). According to reports, hackers accessed their internal corporate IT environment and stole encrypted passwords, a similar approach to what the same group reportedly did in the Microsoft breach earlier this year.
TeamViewer provides remote access and remote-control software to around 640,000 customers globally, from large enterprises to small companies. Many of these customers, especially the large enterprises, are likely examining the potential impacts of this recent hack on their own networks today and in the days and weeks ahead.
As supply chains increase in complexity, answers to the problem seem more elusive.
The fact that supply chain is an increasingly common threat vector for attacks is nothing new – for example, the SolarWinds hack in 2020 impacted over 100 companies. In our conversations with Chief Information Security Officers (CISOs) over the past six months, supply chain risk is consistently mentioned as a top priority.
There is no easy answer. On any day, the average Chief Information Officer (CIO) of a large enterprise manages around 200 software as a service (SaaS) application provided by third parties, and each of these SaaS tools comes with varying degrees of risk to the company that the CISO is responsible for managing.
As digitization and the interconnectedness of global commerce accelerates, this picture only grows more complex. It’s not just a matter of assessing every third party, ranking them as ‘high’, ‘medium’, or ‘low’ risk, or ensuring that internal controls are in place to manage the potential vulnerabilities. The risk picture for the supply chain is as dynamic as it is for the company itself. Because of the scale of threats and attacks facing companies today, not every vulnerability can be considered critical. The average Security Operations Center (SOC) for large companies receives thousands of alerts every day – it’s no wonder that ‘alert fatigue’ is becoming more prominent for CISOs.
What Intangic thinks
So, how is cyber insurance dealing with this problem? Contingent business interruption (CBI) coverage is the primary answer. But, just as the property sector knows, that alone is not sufficient for dealing with the risk, even from a loss recovery perspective, let alone to help reduce the likelihood of an event. The decisive role of insurance shouldn’t boil down to a matter of your policy wording on supply chain or CBI. It’s fair to say that when CISOs think about supply chain risk and events like TeamViewer, a risk program is not on the short list of tools they think of. However, from Intangic’s perspective, it should be.
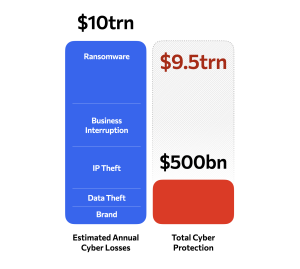
It’s also important to remember that when quantifying a company’s total economic loss risk, this includes the supply chain. The~$10 trillion economic loss number includes business risk factors like cashflows, productivity and earnings for suppliers too.
The Risk Officer and CISO should be linked in the same risk management value chain – not separate, siloed functions that only interact during the annual cyber policy renewals cycle. With new technology, the Risk Officer today can now do more for and with the CISO than provide a measure of loss recovery for the clean-up post-breach.
Here are some specifics of what the Risk Officer can do together with the CISO:
- Improved visibility of risks across supply chain: CISOs tell us that they need improved visibility of the risks across their supply chain on an ongoing basis, not simply as a moment in time snapshot provided by a single risk assessment. The CISO has responsibilities to defend the fortress around the clock, vetting the severity of thousands of incoming alerts while also looking after compliance and board reporting. He or she and the security team need to know where the highest risks exist among those providers. Suppliers that are being attacked more than their respective peers are at higher risk of a large breach and thus post greater vulnerabilities to the companies they service. With the Intangic CyFi™ Dashboard, for the first time Risk Officers can help CISOs see this threat activity at scale across the supply chain every month.
- Enable a Preventative, Early Response: Risk Officers are now able to provide CISOs and the information security team with the ability to prioritize preventative steps to fix problems contributing to any spike in risk levels and encourage their suppliers to do the same – before the large breach occurs. While every company’s supply chain will undoubtedly have vulnerabilities, placing a greater emphasis on more robust threat detection and preventative remediation across a company’s supply chain will strengthen the risk program and overall security.
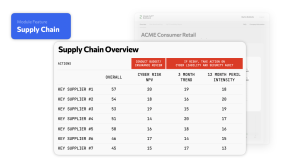
Figure1. Supply Chain feature on Intangic CyFi™ Dashboard
Improving visibility of the risks across supply chains on an ongoing basis
The Risk Officer can now join the CISO to form a stronger line of defence built on risk prevention and early response, including on supply chain risk.